Remote Authentication Dial-In User Service also known as RADIUS is a client-server networking protocol used for authentication in a network. It comprises of two component for it to work which is a client and a server. The client is the device you as an administrators wants people to authenticate while the server would serve this authenitcation request by checking the credentials with it’s database.
Usually the RADIUS client is a NAS while the RADIUS server is a WIndows NT or UNIX machine.
It can be used in both Unix and Windows system to ensure AAA (Authentication, Authorization & Accounting).
It can be used in a home network (NAS) to ensure authentication when accessing the NAS. 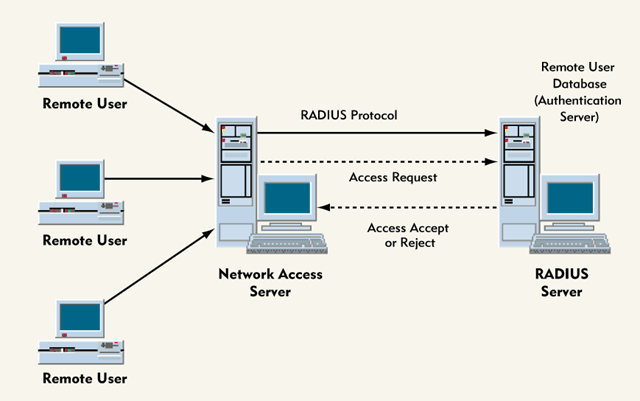
How does it work?
- User sends a form of authentication to the RADIUS Client
- Client prompts for credentials
- User replies with the credentials
- RADIUS client forwards the encrypted credentials to the RADIUS server
- RADIUS server replies with a reply of either
Accept,Reject, orChallenge - RADIUS client then based on the result of the server reply, it performs it’s action
RADIUS vs TACACS+
RADIUS is open source and can be used anywhere while TACACS+ is CISCO proprietary. However, TACACS+ is more secure and reliable as it uses TCP and it fully encrypts packets.
How to get started
A quick, popular and easy way is with FreeRADIUS.
Alternatives to freeRADIUS
- Devise
- Auth0
- 0Auth2
- LoginRadius
Setup
NOTE (Debian based devices would be called freeradius instead of radiusd hence switch the commands from freeradius to radiusd if it does not work)
1. Install the server
1
$sudo apt install freeradius
Debian-based systems
2. Startup the freeradius server(as root)
1
$sudo freeradius -X
NOTE (When there is an error when running the startup)
the error is usually due to a current radius already running, hence we would need to kill it to run the current freeradius
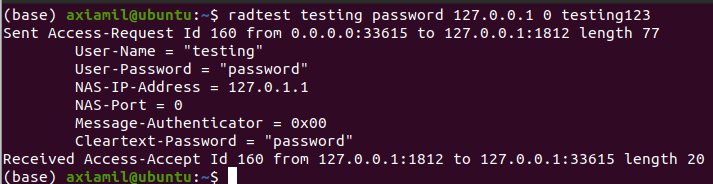
3. Testing of freeradius
To test the freeradius, we can use the radtest commands
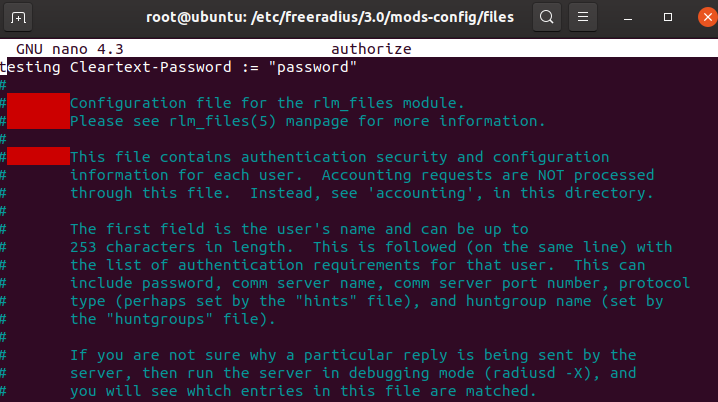
firstly, edit the raddb/mods-config/file/authorize and add the following line of text at the top of the file, before anything else
1
testing Cleartext-Password := "password"
1
$radtest testing password 127.0.0.1 0 testing123
4. Adding clients
To add a client edit the clients.conf file by adding the following content
1
2
3
4
5
client new {
ipaddr = 192.0.2.1
secret = testing123
shortname = testing
}
change the ip address to the client ip address and the secret to the password that you want to use use ipv6addr for IPv6 Address instead of ipaddr
More info
Main configuration file is called radiusd.conf in the root folder of the freeradius file Listening, Proxy, Authentication configuration are in the sites-available/default file